GP IT systems switched off for patching in parts of England
- 15 May 2017

NHS staff working GP practices in parts of England have been told to keep their systems switched off until patches against the ‘WanaDecrypter’ ransomware can be applied.
Despite many NHS staff working over the weekend to update and protect systems by applying patches, primary care services looked set to be severely disrupted this morning as GP practices return to work.
On Monday morning, NHS Digital sent to all GP practices a “guidance note” that included available patches and a ‘Guide to patching’.
Professor Helen Stokes-Lampard of the Royal College of General Practitioners said: “GPs, of course, can still diagnose and treat patients without using computers but we ask our patients to bear with us if routine services such as repeat prescriptions and appointment booking services are slightly disrupted this week”.
In the north east primary care organisations were advised last night to put contingency plans into action, and advised they will not have access to GP IT systems on the NHS N3 Network until this evening.
The advisory from the commissioning support unit (CSU) told staff they will not have access to clinical systems; to stack all referrals; “only request urgent diagnostics as these will have to be done manually”. Similarly, electronic appointments will not be available.
“Primary care organisations across the North East will not have access to IT systems tomorrow (Monday 15 May 2017) and we are working hard to restore these throughout the day. If you’ve not already done so please activate your business continuity plans immediately.”
Primary care staff were advised to switch on their computers but not log-in and not to try and apply patches themselves. By Sunday night one-third of the 390 practices in the north east had received patches.
A spokeswoman from Midlands and Lancashire CSU told Digital Health News on Monday morning that GPs were being advised to shut down their computers if they see ransomware, and label it as quarantined, and not to use it until a roving IT help team has looked at it. Practices are also being told to tell IT help teams which are the business critical systems.
In her region, the spokeswoman said, there was a range of computers per CCG affected with some having one, and others 28.
Some GP practices may be experiencing disruption to services due to the cyberattack on 12/5/17. Please use NHS services wisely at this time.
— Central Lancashire NHS (@NHSCentralLancs) May 15, 2017
Great Preston clinical commissioning group (CCG) said on Monday morning that “GP practices in Greater Preston are experiencing some disruption to services”.
“IT engineers are supporting practices to get their systems back up and running as quickly as possible, but some electronic call queuing systems may have been affected, so patients may experience some delays in getting through to practices. If this happens, please keep trying.”
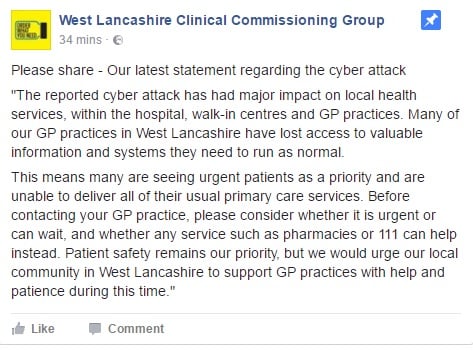
West Lancashire CCG posted on Facebook on Monday morning saying the cyber-attack “has had a major impact” and that access to health IT systems has been lost.
“Many of our GP practices in West Lancashire have lost access to valuable information and systems they need to run as normal.”
Liverpool CCG said on Twitter that Liverpool practices are operating normally, with a spokeswoman confirming to Digital Health News that the message to practices is “business as usual” but remain vigilant.
Delighted to report that Liverpool practices are operating normally today with no complications from the #NHScyberattack on friday.
— One Liverpool (@_OneLiverpool) May 15, 2017
However, Digital Health News understands that the backlog from the cyber-attack could take six to eight weeks to clear.
Blackburn with Darwen CCG has also reported on Monday morning that pharmacies have been affected by the cyber-attack.
Primary care systems supplier EMIS advised: “There is no evidence to suggest that EMIS Health systems have been compromised or impacted as a result of this incident.” TPP issued a near-identical statement “There is no evidence to suggest that SystmOne or SystmOnline have been affected by ongoing incidents.”
In a letter to NHS chief executives issued Sunday night, Jim Mackey chief executive of NHS Improvement, and Will Smart, NHS chief information officer, advised not connecting unpatched machines to networks and leaving them switched off until patches can be applied.
“You should make a risk-based decision on whether unpatched PCs, windows-enabled devices, and relevant imaging and pathology devices should be disconnected from the network. Leaving unpatched machines on the network heightens the risk of infection and you would need to consider whether other controls such as Anti-Virus and Firewalling offer the appropriate mitigation. In the event you cannot be assured of this, you should consider running them in ‘standalone’ mode. You can contact NHS Digital for further advice.”
Chief executives were told “All unpatched devices make your IT estate vulnerable”, and urged to identify “the number of PCs and other windows-enabled devices that are within your estate” and “the number that have been infected with the ransomware”.
In addition, they are urged to identify how many PCs and other windows-enabled devices “have been patched and cleansed, and the number for which this process has not been carried out”.
And highlighting concerns that diagnostic and imaging devices may also be vulnerable, they are also asked how many windows-enabled diagnostic imaging and pathology devices have been patched and cleansed, and how many still need to be.
Where patches have not been applied across the IT estate they are asked to ensure they are applied “as a matter of urgency”.
Other regions in England are less affected than the north west.
Dorset CCG has reported on Monday “that the ransomware attack has had little impact on the health community in Dorset, however we continue to be vigilant”.
Latest guidance from NHS Digital
NHS Digital letter explaining patches to protect against cyber attack [293.39Kb]
Technical guide for patching to protect against cyber attack [533.76Kb]
Responses to FAQs on the cyber attack on the NHS 12 May 2017 [408.13Kb]





2 Comments
That’s a bold statement. If you have stopped it though, at the mail gateway,, do you mind posting a few screenshots of the offender. It would actually help.
Again all these organisations seem to be using local email services instead of NHS.net.
greaterprestonccg.nhs.uk
liverpoolccg.nhs.uk
lancashirecsu.nhs.uk
westlancashireccg.nhs.uk
Security is multilayers this isn’t a Windows specific problem. It’s about the overall approach to IT infrastructure and Security Managment.
Comments are closed.