Davey Winder: ransomware, it’s over here
- 15 November 2016
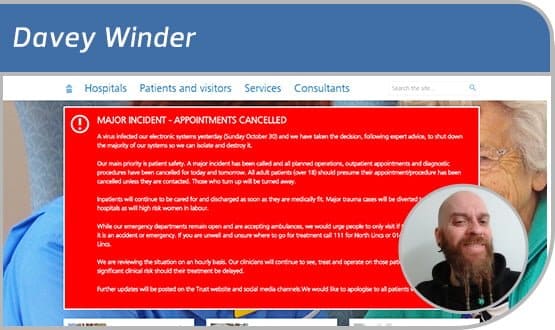
Northern Lincolnshire and Goole NHS Foundation Trust has secured itself a footnote in the history of healthcare IT that it probably didn’t want.
It has become the first organisation to make national headlines for suffering a virus attack so virulent that it had to all but cease operations. For three days. Just as the government decided to relaunch its cyber security strategy.
The trust has said that "following expert advice" it shut down "the majority of our systems” to “isolate and destroy” the virus.
It hasn’t said much more, and the matter is now in the hands of the police. Nevertheless, one must assume that when it says “a virus”, what the trust means is ransomware.
One also must assume that the expert who was around to give the “isolate and destroy” advice was absent prior to the attack.
Ransomware: a quick recap
Regular readers of this column will not need a recap on what ransomware is, but as a reminder, it’s “a type of malicious software designed to block access to a computer system until a sum of money is paid.”
These attacks have been targeted at individuals and at institutions. The US has a real problem. However, there’s little doubt that ransomware hackers are interested in healthcare on both sides of the pond.
Sure, high value health targets are generally thought to be stateside, but that’s only in terms of a ‘per record valuation’ for stolen patient records.
When it comes to ransomware, the value proposition is in preventing disruption from the health organisation perspective; at least one US hospital is on record for paying out.
In August, the NCC Group published the results of a Freedom of Information request that showed some 28 NHS trusts in England had been the victim of a successful ransomware attack during the past year.
These were ‘successful’ in as far as the attackers managed to encrypt data and demand a ransom. The true number is likely to be higher as only 60 trusts responded, and 31 of them refused to answer the request.
So, we not only know that healthcare UK is a target, but that it has fallen victim to the attack mode in some numbers. The bigger problem is that health trusts must know this, which begs the question: why isn’t more being done to prevent this from happening?
Prevention is better than cure
The saying "prevention is better than cure" might be an old one, but that doesn't make it any the less appropriate here.
As Anton Grashion, a senior director at AI-inspired security vendor Cylance says: “The healthcare industry is clearly still shackled to the “detect and respond” approach.
“Chasing threats after the damage has already been done is not an effective method of dealing with cyber security, especially when people’s health is at stake."
And as Jason Steer, solutions architect at vendor Menlo Security adds: “Instead of isolating a virus after it has infected a network and effectively stopped it from operating, security solutions should be isolating malware before it has a chance to execute and bring major organisations to their knees.”
Sing it loud
While Northern Lincolnshire and Goole was doing battle with its virus problem, another IT director, Jane Berezynskyj, from Papworth Hospitals NHS Foundation Trust, was telling the EHI Live 2016 trade show in Birmingham about a ransomware attack that it saw off.
Reports of her presentation say that a nurse at the world-famous heart and lung hospital clicked on an infected email, activating the attack at about 11pm on a Saturday night.
Fortunately, it did not start encrypting files until after midnight – by which time the trust had completed its daily backup, making it easy to restore its systems.
The trust has still made some changes, such as moving to hourly, incremental backups, and using mixed media, including tapes, to give it more lines of defence.
This experience shows that I’m not being glib when I say that “a spoonful of secure thinking makes the ransomware go down”.
It’s just true. This is pretty simple stuff, after all. Proven backup and recovery processes can prevent any long-term damage to systems and real time file activity monitoring can prevent individual machines from impacting file servers.
Separate critical medical devices and systems from other networks, ensure regular patching hygiene is in place. Oh yes, and educate users.
Berezynskyj told EHI Live the nurse never reported Papworth’s incident. “One of our key weaknesses is our people and user behaviour," she said. Papworth has a programme of staff education and communication.
Trusts are likely to find that they are likely to need they need to run these – and run them again. Even so, this is not new stuff. This is not difficult stuff. Maybe we need to sing it for the message to actually stick?




